Everbe 2.0 Ransomware Decryption – Is it possible?
Ransomware Everbe 2.0 Hacker Characteristics
Everbe 2.0 ransomware is a crypto infection, and its primary objective is to lock up data and need ransom for its the decryption secret.
The cyber threat is a successor of Everbe 2.0 ransomware, which was first potted in March 2018, and revealed up once again several times as Embrace, Embrace, EvilLocker and Hyena Locker.
The infection utilizes AES [1] and RSA file encryption algorithms to secure data. While initial variation used.everbe appendix, the newest version which was discovered in September 2018 uses.NOT _ OPEN file extension,!. txt _ HOW_RECOVERY_FILES ransom note and advises users to call hackers via the notopen@cock.li or tryopen@cock.li e-mails.
Can you decrypt Everbe 2.0 Ransomware encrypted files?
Unlike some previous versions, the most recent ones are regretfully not decryptable yet.
When evaluating the sample it appeared that different antivirus programs spot this danger.
This fact suggests that the finest option for Everbe 2.0 elimination is anti-malware tools or your credible anti-viruses.
It is possible that ransomware disturbs your antivirus, so you may need to go into the Safe Mode before scanning the system.
You can see this approach more in dept on the guide listed below the post.
Unfortunately, there is no known method to decrypt files encrypted by Everbe 2.0 without paying the ransom and obtaining the private RSA keys from the criminals since they fixed the flaws and Demonslay335’s decypter for Everbe 1.0 will not work.
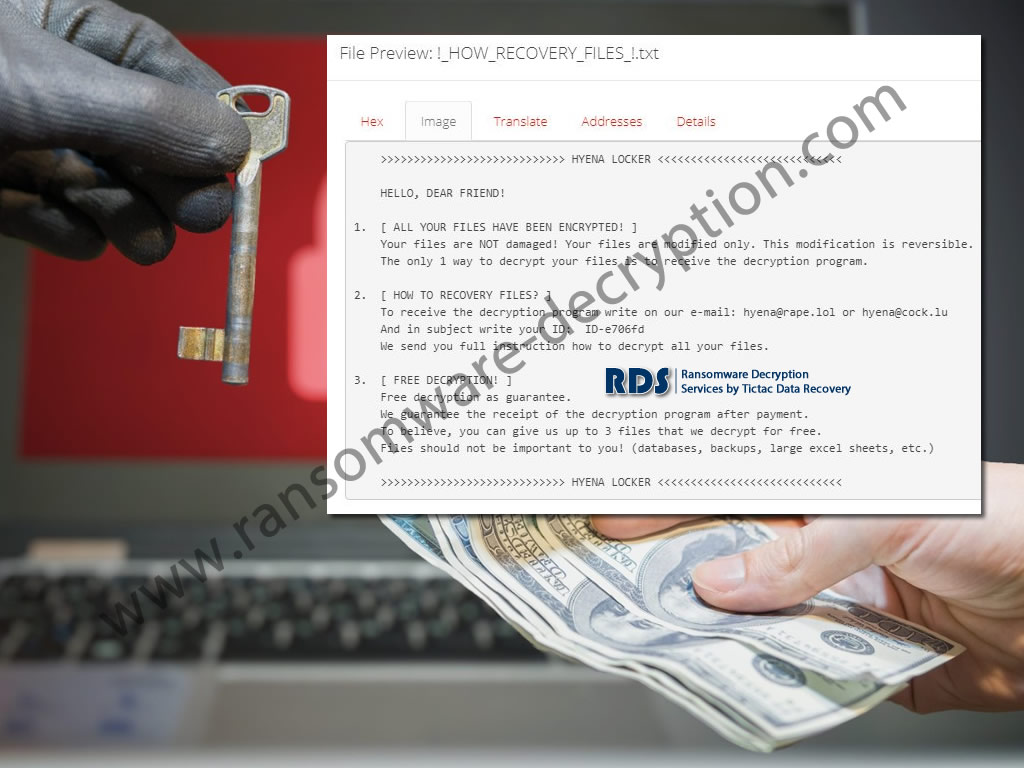
Everbe 2.0 Ransomware Note
The most recent variation of Everbe 2.0 ransomware displays the ransom note which reads the following:
>>>>>>>>>>>>>>>>>>>>>>>>>>>> NOT_OPEN LOCKER <<<<<<<<<<<<<<<<<<<<<<<<<<<<
HELLO, DEAR FRIEND!
1. [ ALL YOUR FILES HAVE BEEN ENCRYPTED! ]
Your files are NOT damaged! Your files are modified only. This modification is reversible.
The only 1 way to decrypt your files is to receive the decryption program.2. [ HOW TO RECOVERY FILES? ]
To receive the decryption program write to email: notopen@cock.li
And in subject write your ID: ID-[redacted 10 hex]
We send you full instruction how to decrypt all your files.
If we do not respond within 24 hours, write to the email: tryopen@cock.li3. [ FREE DECRYPTION! ]
Free decryption as guarantee.
We guarantee the receipt of the decryption program after payment.
To believe, you can give us up to 3 files that we decrypt for free.
Files should not be important to you! (databases, backups, large excel sheets, etc.)>>>>>>>>>>>>>>>>>>>>>>>>>>> NOT_OPEN LOCKER <<<<<<<<<<<<<<<<<<<<<<<<<<<<
How Everbe 2.0 is identified by antivirus software?
This NOT OPEN LOCKER virus that belongs to Everbe ransomware and it might show up after the scan like this:
- Generic.Ransom.Everbe.3D90239A;
- Win32:Malware-gen;
- HEUR/AGEN.1031998;
- Trojan.Win32.Generic!BT;
- W32/Trojan.YOEK-2696;
- W32/Filecoder.NQU!tr.
Emails used by the Hackers
The emails you can see that usually used for Everbe 2.0 are the following:
- hyena@rape.lol
- hyena@cock.lu
- notopen@cock.li
- eV3rbe@rape.lol
- divine@cock.lu
- tryopen@cock.li
These are the extensions of Everbe 2.0 Ransomware
- .eV3rbe
- .EVIL
- .HYENA
- .thunder
- .divine
What is the price for decrypting Everbe 2.0
This is the first reply that we got from Everbe 2.0 Hacker team:
We can decrypt your data, here is price:
– 3 Bitcoins in 30 hours.
– 4 Bitcoins if you need more than 30 hours to pay us, but less than 72 hours.
– 5 Bitcoins if you need more than 72 hours to pay us. Pay us and send payment’s screenshot in attachment.
In this way after you pay we will send you decryptor tool with instructions.
TIME = MONEY.
If you don’t believe in our service and you want to see a proof, you can ask about test decryption.
About test decryption:You have to send us 3 crypted file.
Use http://dropmefiles.com/ to and Win-Rar to send file for test decryptions.
File have to be less than 10 MB.
We will decrypt and send you your decrypted files back.
Answer us with your decision.
Attention!
Do not rename encrypted files.
Do not try to decrypt your data using third party software, it may cause permanent data loss.
Decryption of your files with the help of third parties may cause increased price
(they add their fee to our) or you can become a victim of a scam.
Time limit starts from this email.
Here is our bitcoin wallet:
1HwThynfxnCnV3eWBcxPAYwAFP8d7FMrAg
Places to buy Bitcoins and beginners guide here:
https://www.buybitcoinworldwide.com/ – Start from here.
http://www.coindesk.com/information/how-can-i-buy-bitcoins
can recommend easy bitcoin exchange service – localbitcoins.com (HOW TO BUY BITCOINS: https://localbitcoins.com/guides/how-to-buy-bitcoins )
or you can google any service you want.
Please write your answer right away!
Everbe 1.0 can be decrypted for free
- You can find decryptor here that will work in some circumstances of Everbe 1.0
- Also you may try to decrypt with this decryptor
Evaluation of Hacker Team behaviour in negotiation
Unfortunately the Hacker Team of Everbe 2.0 seems a bit aggressive and cannot settle to an amount that can be easily paid.
Also we have no evidence that the Hacker team will be honest and send the files after payment.
If you have an Everbe 2.0 Ransomware Incident you can consult our team on how you can proceed or recover some files partially.
Resources
Leave a Comment
(6 Comments)
Good evening ,
I would like your help with my customerwho was infected by ransomware everbe 2.0
The attack took place on the central server and all files were changed to [evilcock@cock.li] .evil
You can help ?
Hi there my sql databases have been encrypted with everbe 2.0 (.thunder). I only need to decrypt just one database don’t care about files or anything else. Is there a way to decrypt such a file (MS SQL database).
Thank you
Hello sir, please send us your name and contact number (Phone/Viber/Skype/Whatsapp). 1 sample encrypted file (.docx,.doc,.xlsx,.xls) under 500kb in info@ransomware-decryption.com so that we can send you what we need for the preliminary free evaluation.
Hello sir, please send us your name and contact number (Phone/Viber/Skype/Whatsapp). 1 sample encrypted file (.docx,.doc,.xlsx,.xls) under 500kb in info@ransomware-decryption.com so that we can send you what we need for the preliminary free evaluation.
We can try manual decryption of the database, as long as you have a backup from an earlier and unencrypted version of the database. You can send us some sample and we can check it out.
We can definately help. But please our contact phone or email to submit such incidents. If you comment to our blog, we will probably miss it.
Recent Posts
Recent Comments
Archives
Categories
Meta
Amazing WodPress Themes!
View our themes here.
Buy ThemeRecent Posts
Send us an email
+306932237053
Recent Posts
Recent Comments
Archives
Categories
Meta
Amazing WodPress Themes!
View our themes here.
Buy ThemeRecent Posts