What is Ryuk Ransomware ?

Ryuk is one of the next generation ransomware variants that is mainly used for custom and targeted attacks primarily on very big firms & organizations that usually bring more profits to the criminals. It has been spreading since August 2019 but many big attacks were made in 2019.
Ryuk Ransomware encryption targets critical files & resources so that it can achieve maximum damage while its malicious code is released manually by the hackers, once they know they have stolen all the appropriate credentials from the infrastructure.
Ryuk is one of the most expensive Ransomware in terms of Ransomware amount demand, targets large organizations and medium to large-sized businesses.
Is the decryption without paying the ransom possible?
Unfortunately as for now there is no decryption software (Ryuk Decryptor) and even if an organization decides to pay its decryption process has a lot of problems.
Ryuk Ransomware hackers behavioural analysis shows that they don’t just shoot and go.
They penetrate the infrastructure that they want to blackmail and then they stay in there for quite some time in order to see if the network infrastructure is a good target for them.
If they find a good target which will be then blackmailed for Ransom, then they compromise all defences, deactivate protection, find and compromise both live systems but also backup infrastructure and when they are ready they push the button for encrypting the files.
Ryuk has claimed several high-profile victims since the fall of 2018, including newspapers such as the Chicago Tribune and the Los Angeles Times, the city of Stuart, Fla. and Onslow Water and Sewer Authority.
Ryuk Ransomware Note
The Ryuk ransom relies on a file called: RyukReadMe.txt or UNIQUE_ID_DO_NOT_REMOVE.txt
There are many templates that have been used for the ransomware note.
Usually the Hackers address is hosted in protonmail.com or tutanota.com.
Also it has been observed that some of the templates are very similar to BitPaymer Ransomware ransom notes, an older variant.
As of this writing, it remains unclear if GRIM SPIDER is copying the TTPs (tactics, techniques and procedures) and ransom notes of BitPaymer, or whether the groups may share information with each other.
Version 1 Ryuk Ransomware Note Template
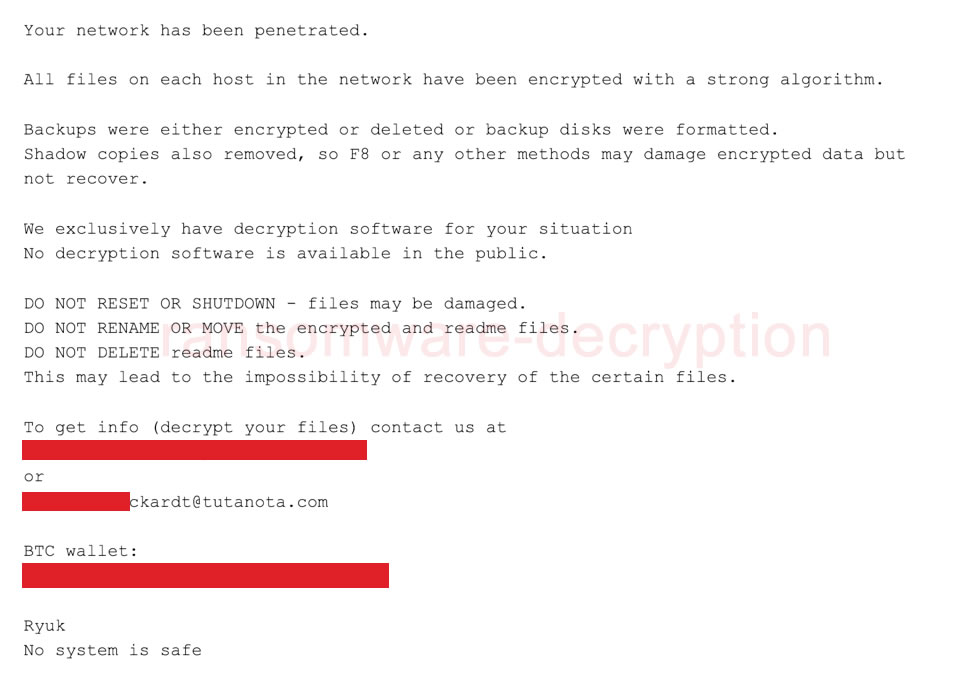
All files on each host in the network have been encrypted with a strong algorithm.
Backups were either encrypted or deleted or backup disks were formatted.
Shadow copies also removed, so F8 or any other methods may damage encrypted data but not recover.
We exclusively have decryption software for your situation
No decryption software is available in the public.
DO NOT RESET OR SHUTDOWN – files may be damaged.
DO NOT RENAME OR MOVE the encrypted and readme files.
DO NOT DELETE readme files.
This may lead to the impossibility of recovery of the certain files.
To get info (decrypt your files) contact us at
MelisaPeterman@protonmail.com
or
MelisaPeterman@tutanota.com
BTC wallet:
[link]
Ryuk
No system is safe
Version 2 Ryuk Ransomware Note Template
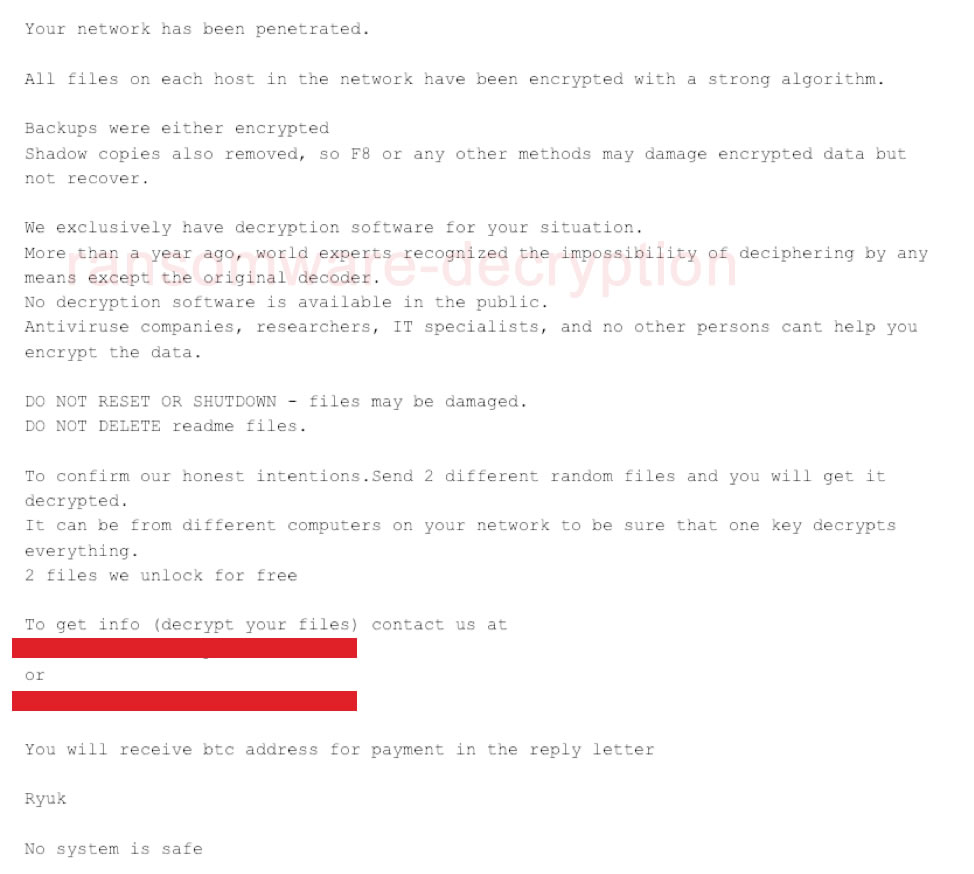
Gentlemen!
Your business is at serious risk.
There is a significant hole in the security system of your company.
We’ve easily penetrated your network.
You should thank the Lord for being hacked by serious people not some stupid schoolboys or dangerous punks.
They can damage all your important data just for fun.
Now your files are crypted with the strongest millitary algorithms RSA4096 and AES-256.
No one can help you to restore files without our special decoder.
Photorec, RannohDecryptor etc. repair tools are useless and can destroy your files irreversibly.
If you want to restore your files write to emails (contacts are at the bottom of the sheet) and attach 2-3 encrypted files
(Less than 5 Mb each, non-archived and your files should not contain valuable information
(Databases, backups, large excel sheets, etc.)).
You will receive decrypted samples and our conditions how to get the decoder.
Please don’t forget to write the name of your company in the subject of your e-mail.
You have to pay for decryption in Bitcoins.
The final price depends on how fast you write to us.
Every day of delay will cost you additional +0.5 BTC
Nothing personal just business
As soon as we get bitcoins you’ll get all your decrypted data back.
Moreover you will get instructions how to close the hole in security and how to avoid such problems in the future
+ we will recommend you special software that makes the most problems to hackers.
Attention! One more time !
Do not rename encrypted files.
Do not try to decrypt your data using third party software.
P.S. Remember, we are not scammers.
We don’t need your files and your information.
But after 2 weeks all your files and keys will be deleted automatically.
Just send a request immediately after infection.
All data will be restored absolutely.
Your warranty – decrypted samples.
contact emails
eliasmarco@tutanota.com
or
CamdenScott@protonmail.com
BTC wallet:
[link]
No system is safe
How the decryptor Works [Video]
What happens when Ryuk Ransomware infects a system?
In the following video you will see how Ryuk Ransomware infects the computer and encrypts the files:
Ryuk hacker emails
- CamdenScott@protonmail.com
- CamdenScott@protonmail.com
- MelisaPeterman@tutanota.com
If we cannot decrypt then what can we do for Ryuk Ransomare encrypted files?
Our ransomware incident response team can help as an external consultant, assess the situation and understand if there is an alternative.
Contact us for a free consultation.
References to Ryuk Ransomware Incidents:
- How a Manufacturing Firm Recovered from a Devastating Ransomware Attack
- Multiple Hospitals in the US Shut down due to Ransomware Attack
- Ryuk Ransomware Cripples MSP and Major Newspapers, Represents Dangerous Shift Toward Coordinated Attacks
- DCH Hospital Pays Ryuk Ransomware for Decryption Key
- Technical Analysis of Ryuk Ransomware from Crowdstrike