Ransomware Hacker Reviews Email Database
Is a hacker reliable or not ? Based on Hacker Email Database
- backtonormal@foxmail.com
- Beamsell@qq.com
- bebenrowan@aol.com
- Badfail@qq.com
- bitcoin888@cock.li
- bkp@cock.li
- black.mirror@qq.com
- Blacklist@cock.li
- Blammo@cock.li
- BM-2cXonzj9ovn5qdX2MrwMK4j3qCquXBKo4h@bitmessage.ch
- btc2017@india.com
- btcdecrypter@qq.com
- combo@tutanota.de
- cooldesktop@cock.li
- cooldesktop@protonmail.com
- cyberwars@qq.com
- Darknes@420blaze.it
- decrypt_arena@india.com
- decryptdata@qq.com (STOP .djvu)
- decryptoperator@gmail.com
- decryptprof@qq.com
- decryptinfo@protonmail.com
- decryptseller@gmail.com
- doololostme1986@aol.com
- evillocker@cock.li
- gladius_rectus@aol.com
- goodjob24@foxmail.com
- Grizzly@airmail.cc
- help_files@aol.com
- icrypt@cock.li
- johnrant@gmail.com
- kyratsas@gmail.com
- lassvegas@protonmail.com
- marat20@cock.li
- mazma@india.com
- nigmut@ganefs.com
- paydecryption@qq.com
- paymentbtc@firemail.cc
- payransom@qq.com
- pdfhelp@india.com
- sasutemul1972@aol.com
- savefiles@india.com
- sebekgrime@tutanota.com
- stopencrypt@qq.com
- suppfirecrypt@qq.com
- tracsebluopa1975@aol.com
- veradecrypt@gmail.com
- WindyHill@cock.li
- youneedfiles@india.com
- kromber@tutanota.com (email shut down)
- DonovanTudor@aol.com (Phobos)
- kromber@india.com (email shut down)
- Sqlbackup4@mail.fr (Phobos)
- wolfhelp359@airmail.cc (Wolf)
- luciolussenhoff@aol.com (Phobos)
- zorsesecurity@airmail.cc
- zorsesecurity@mail2tor.com
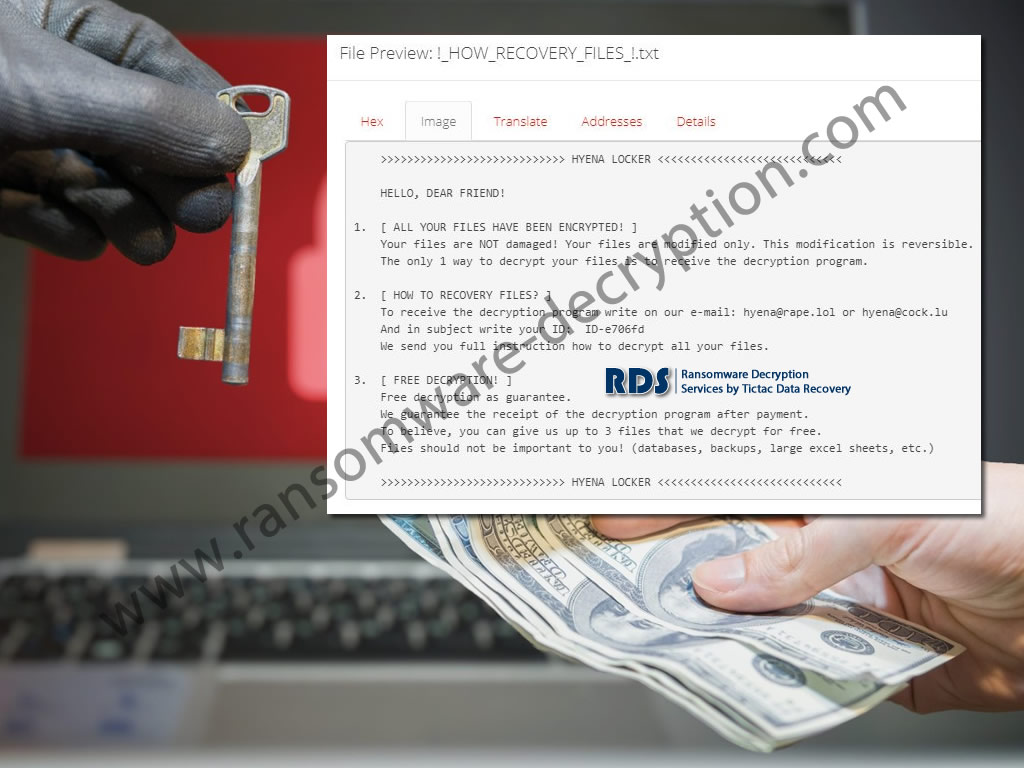
- hyena@rape.lol (everbe 2.0)
- hyena@cock.lu (everbe 2.0)
- notopen@cock.li (everbe 2.0)
- eV3rbe@rape.lol (everbe 2.0)
- divine@cock.lu (everbe 2.0)
- tryopen@cock.li (everbe 2.0)
Encrypted file samples from Dharma (.cezar) Ransomware
- .id–A04EBFC2.[bitcoin143@india.com].dharma
- .id–480EB957.[legionfromheaven@india.com].wallet
- .id–EB214036.[amagnus@india.com].zzzzz
- .id–5FF23AFB.[Asmodeum_daemonium@aol.com].onion
- .id–01234567.[gladius_rectus@aol.com].cezar
- .id–01234567.[btc2017@india.com].cesar
- .id–BCBEF350.[chivas@aolonline.top].arena
- .id–BCBEF350.[cranbery@colorendgrace.com].cobra
- .id–406B4F5A.[black.mirror@qq.com].java
- .id–30B3DDC1.[mazma@india.com].write
- .id–B8F053EC.[marat20@cock.li].arrow
- .id–BCBEF350.[Beamsell@qq.com].bip
- .id–FCOA3387.[combo@tutanota.de].combo
- .id–BCBEF350.[paymentbtc@firemail.cc].cmb
- .id–A0B3FFC4.[paydecryption@qq.com].brrr
- .id–BCBEF350.[bebenrowan@aol.com].gamma
- .id–BCBEF350.[icrypt@cock.li].monro
- .id–BCBEF350.[bkp@cock.li].bkp
- .id–BCBEF350.[btc@fros.cc].btc
- .id–BCBEF350.[decrypt@fros.cc].bgtx
- .id–BCBEF350.[decrypt@fros.cc].boost
- .id–BCBEF350.[Darknes@420blaze.it].waifu
- .id–8ADB6DDA.[WindyHill@cock.li].funny
- .id–BCBEF350.[backtonormal@foxmail.com].betta
- .id–BCBEF350.[Blacklist@cock.li].vanss
- .id–BCBEF350.[GetDataBack@fros.cc].like
- .id–BCBEF350.[help@decrypt–files.info].gdb
- .id–BCBEF350.[syndicateXXX@aol.com].xxxxx
- .id–30CE2F6F.[unlock@fros.cc].lock]
- .id–BCBEF350.[decrypt@fros.cc].adobe
- .id–B4BCE79D.[payransom@qq.com].AUDIT
- .id–B4BCE79D.[decrypt_arena@india.com].cccmn
- .id–001DBF12.[xtron@cockli].tron
- .id–BCBEF350.[decrypt@fros.cc].back
- .id–001DBF12.[Grizzly@airmail.cc].Bear
- .id–001DBF12.[suppfirecrypt@qq.com].fire
Emails from Phobos Ransomware
- .id[A0BE1E93-1127].[DonovanTudor@aol.com].txt
- .id-9CA00B4E.[Sqlbackup4@mail.fr].bat
- .id[EAFB2DAC-1023].[luciolussenhoff@aol.com].phobos
- .ID–3EA0B923.[job2019@tutanota.com].phobos
- .ID–1ECFD954.[FobosAmerika@protonmail.ch].Frendi
- .ID–2CA6D4CB.[prejimzalma1972@aol.com].phoenix
- .id[B29F13F3–1130].[fileb@protonmail.com].mamba
- .id[F6DE80A3–1148].[karlosdecrypt@outlook.con].KARLOS
- .id[FA10CE41–1104].[kew07@qq.com].ACTIN
- .id[F6DE80A3–1148].[returnmefiles@aol.com].ACTOR
- .id[70C80B9F–1127].[DonovanTudor@aol.com].com
- .id[70C80B9F–1127].[wewillhelpyou@qq.com].adage
- .id[C4BA3647–2243].[walletdata@hotmail.com].WALLET
- .id[6C21BD38–1096].[lockhelp@qq.com].acute
- .id[6C21BD38–1096].[Supportcrypt2019@cock.li].Adame
Emails from Matrix Ransomware
- kromber@india.com
- kromber@protonmail.com
.arrow Ransomware
- .id-{id}.[bitcoin888@cock.li].arrow
- .id-{id}.[Blammo@cock.li].arrow
- .id-{id}.[vauvau@cock.li].arrow
THT Ransomware
- m4xroothackerteam@protonmail.com
Everbe 2.0 Ransomware
- .eV3rbe
- .EVIL
- .HYENA
- .thunder
- .divine
Wolf Ransomware
- .WOLF (wolfhelp359@airmail.cc)
Zorssecurity Ransomware
- .zorsesecurity

Recent Comments